KMS
Links
You can find the PDF containing all my research here. The code used can be found here.
Description
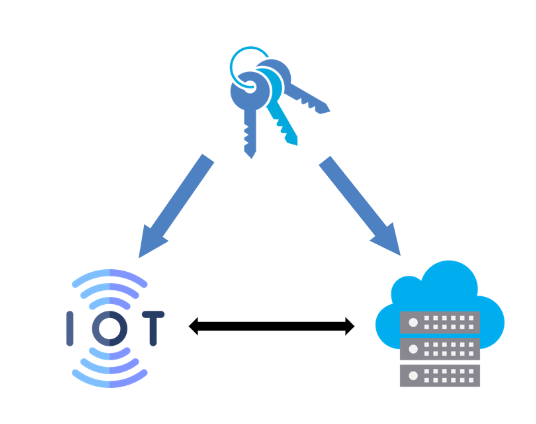
This project was conducted as part of my engineering studies. It aimed to secure cloud and IoT data while preserving their confidentiality by designing a KMS solution.
Objectives
The main objective was to design a Key Management System (KMS) solution to secure data stored in the cloud and on IoT devices, while ensuring confidentiality against potential attackers and cloud service providers.
Context
Today, the cloud is ubiquitous and widely used worldwide, but data privacy remains a major concern. Although cloud service providers claim not to access our data without authorization, legitimate questions remain, especially when our data is accessible in plain text via web portals or cloud service providers’ command interfaces.
Methodology
To successfully carry out this project, I had to implement a rigorous work methodology. Given the broad topic, I first had to select the key information and narrow down the scope of the information I would keep and address in this research. Additionally, I was able to read numerous research articles and content on the subject. Therefore, it was necessary to consolidate everything in one place, annotate important passages, and most importantly, verify my sources.
Technologies Used
Google DriveYoutubePythonJupyter
Results
This work allowed me to better understand the current state of cloud computing and the major challenges it poses in terms of data privacy. I also discovered very interesting techniques to enhance security and ensure data confidentiality. However, these methods have a major drawback: they significantly slow down processing, which partly explains their low adoption to date.
As part of this project, I conducted an in-depth analysis of the IoT and cloud markets today. I identified potential data privacy issues and proposed solutions that I then tested and integrated into a final architecture suitable for the context.
Conclusion
I am particularly proud of this project because the research required to achieve these results was complex and challenging. Resources available on the Internet are often limited, making access to thesis topics difficult. Nevertheless, I found this topic extremely interesting and very relevant in the current context.
However, this project is not without its flaws. Due to time constraints, I was unable to conduct all the comparisons I would have liked or develop the architecture as deeply as I had envisioned.